
My Homelab
I run a Proxmox cluster that currently consists of 2 nodes but will hopefully be adding 1 more node to the cluster to be able to use High Availability, which, if one of the nodes goes offline, will cause the VMs (virtual machines) to be migrated to another node or nodes. One way to improve performance while migrating would be to have a strong backbone of my network with one dedicated NIC on each node to migrate VMs while other running VMs maybe using the other NIC.
What services am I running? I have most of these on Proxmox cluster, which runs Plex, 2 Minecraft servers (which are port forwarded), this website, Tailscale (VPN to access LAN), Openspeedtest https://speedtest.benbernhardt.com, and Uptime Kuma.
Where is THIS Website Hosted?
Well, it is actually hosted in my basement on a Proxmox VM using Ubuntu server for the OS. When first setting up my website, I port-forwarded the machine but later changed it to go through a Cloudflare tunnel (proxy) for additional security against DDOS attacks.
Network
My network is separated into what I call my own “datacenter,” which lets me open ports without risking the safety of all my main devices. Looking at my home network, I have 3 U6 lites, which are all POE (powered over ethernet). The main router runs on bare metal (no hypervisor) and I’m using OPNsense firewall, which also does DHCP and DNSmasq (DNS caching). My main switch is a Cisco 2960g 48 port. My secondary switches are TP-link 8 port and unifi flex mini.

I had to terminate new RJ45 ends on my CAT5e cables, which run to the access points. Which were tested that each cable was connected correctly. To add a little redundancy to my main network, I connect my main OPNsense router to my secondary and then configured a gateway group that switches when there’s packet loss on my tier 1 connection. The failover connection is usually used with 2 ISPs, which, if I did have 2 ISPs, I could do load balancing to make my connection to the internet faster and also more reliable.
To move my servers off the floor, I had to move 8 ethernet cables to another room, and I had keystones to pass the cables through to the other side of the wall. I pulled the 8 cables through a previous hole, which has a box where I connected all 8 cables. On the other side of the wall I have my server rack, which now on the wall there's ethernet ports that lead to that box. My server rack has a patch panel, which all the ethernet is connected to then to my cisco switch.
Monitoring
My monitoring is locally hosted using uptime kuma which gives a good dashboard and alerts me through Discord webhook. I have 5 uptime kuma and one master, which the 5 are on each separate network and the master checking if all 5 are up. One of them is at someone else's house to check if my house is down.
Testing
For testing my networks, I use Open Speed Test, which is self-hosted inside my network to test the local connections. I also have it running through a Cloudflare tunnel, but because it runs through one of my free Cloudflare tunnels, it is limited on how fast it runs. For testing internet speed, I use speedtest.net or fast.com, BUT I only use fast.com because it is faster to type in or ask someone to type in, and it starts automatically.
For testing cables and finding cables, I use a finder tool that also checks if the cable is correctly terminated. Testing Disks I use Crystal Disk Info and Crystal Disk Mark, which tells me how many writes and reads a drive has, and the other one tests how fast a drive is.
Cyber Security
For external connections, most of the time, I use Tailscale for any web GUI or SSH. The main reason I use Tailscale and not other VPN software is because of security; Tailscale doesn’t require port forwarding and has 2FA through Google auth, which I use a 2uf key. When on LAN on my two primary networks, I use OpenVPN to do site-to-site connections. If I need to use a computer with a desktop, I am using Anydesk, which has time-based 2FA.
For WIFI security, I'm using WPA3 personal, which doesn't let attackers deauthenticate clients and makes cracking the 4-way handshake hard because every time, the attacker has to talk back to the access point. I have tried using WPA3 Enterprise, which uses a RADIUS server for the authentication process. The nice thing about using a RADIUS server is that it is possible to specify the IP address, DNS server, and gateway for each user.
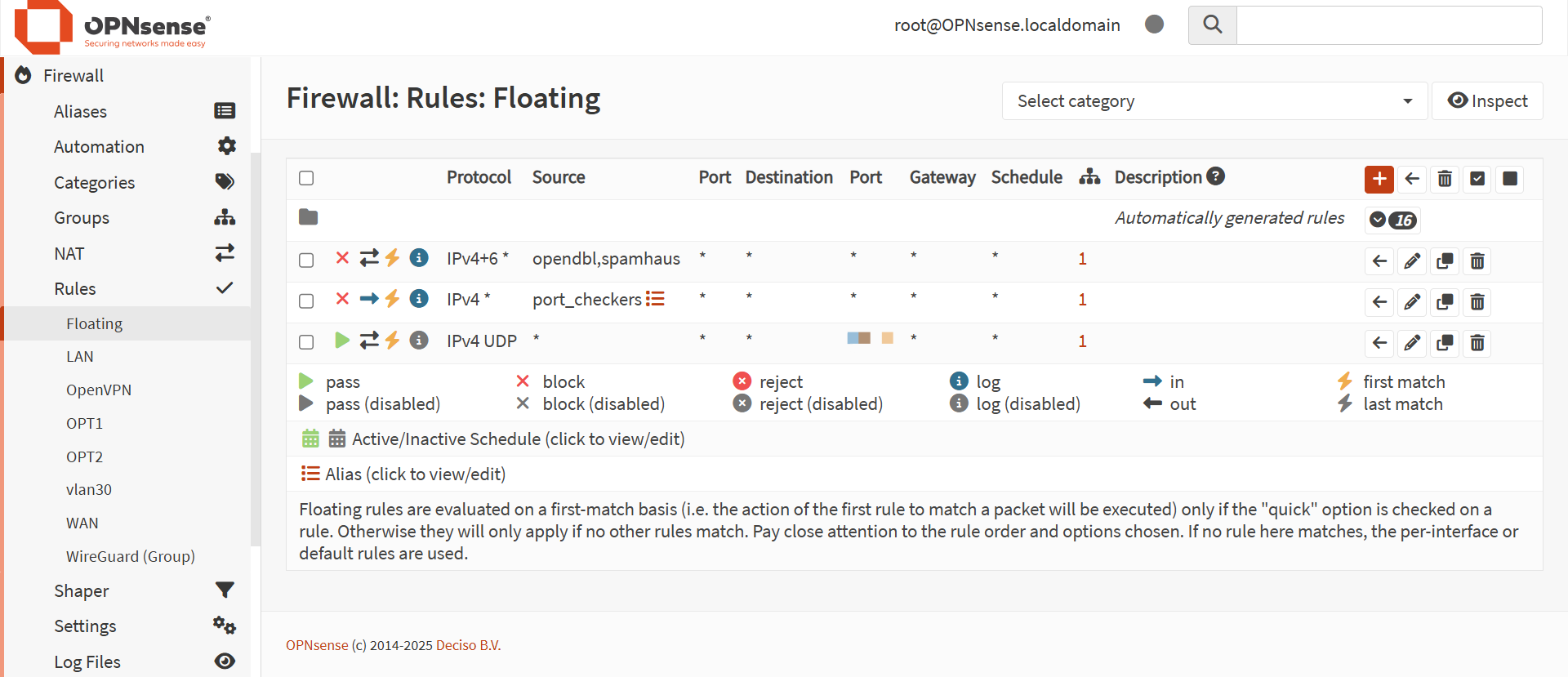
I use OPNsense for my firewall, and I have blocked IPs from the opendbl and spamhaus which have many different reasons to be blocked like botnets, emerging threats, and other malicious activity. I have created my own blacklist of IPs for port scanner websites so anyone using the bigger port scanner website won't be able to map the open ports I have open for my VPN and other services.


